The notorious Lazarus Group, a North Korean hacking organization, has been identified as the culprit behind a recent cyber attack aimed at cryptocurrency investors. This sophisticated campaign, unveiled by Kaspersky researchers, involves a complex series of tactics including social engineering, a deceptive game website, and the exploitation of a zero-day vulnerability in Google Chrome.
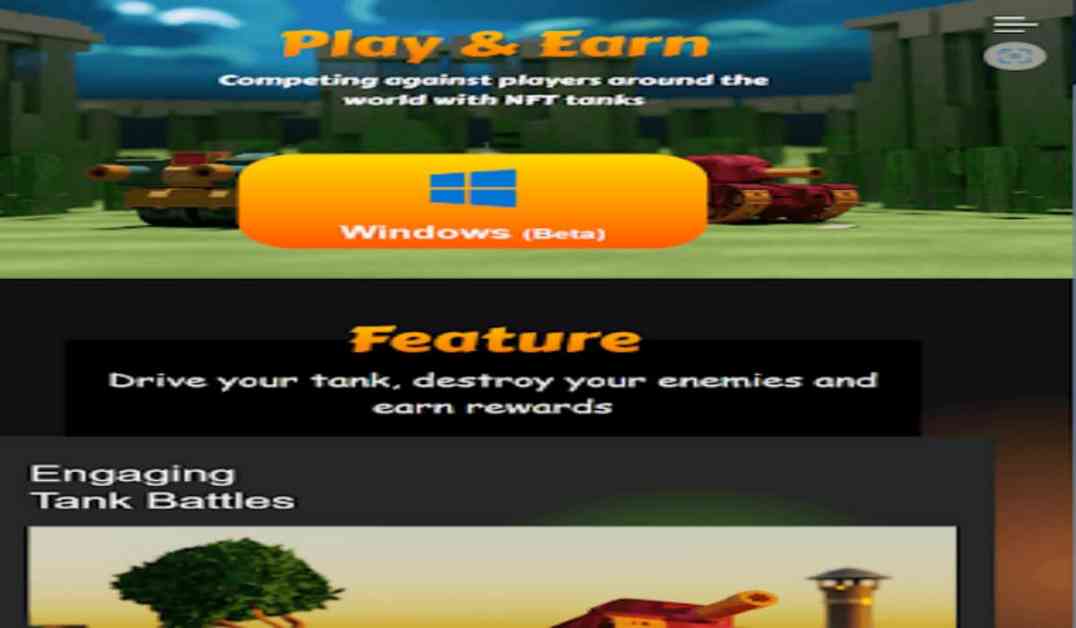
The attack was first detected by Kaspersky Total Security in May 2024 on the personal computer of a Russian individual, who fell victim to the Manuscrypt backdoor. Further investigation by researchers Boris Larin and Vasily Berdnikov revealed that the campaign had commenced in February 2024. The attackers had set up a website named “detankzonecom,” posing as a platform for the fictitious “DeFiTankZone” game.
This fake game purported to merge elements of Decentralized Finance (DeFi) with Non-Fungible Tokens (NFTs) in a Multiplayer Online Battle Arena (MOBA) environment. The website even offered a downloadable trial version to lure unsuspecting users. However, unbeknownst to visitors, the site harbored a hidden script that exploited a zero-day vulnerability in Google Chrome, granting the hackers full control over the victim’s computer.
The exploit targeted two vulnerabilities, one enabling access to the Chrome process’s entire address space from JavaScript (CVE-2024-4947) and the other allowing the bypassing of the V8 sandbox to access memory beyond the register array. Although Google had patched CVE-2024-4947 in March 2024, it remains unclear whether the attackers had prior knowledge of the vulnerability or had discovered it independently.
After successfully compromising a system, the attackers deployed a custom script to gather information about the infected device and assess the presence of valuable assets for further exploitation. The exact nature of the subsequent payload remains undisclosed.
In their pursuit, Lazarus Group focused on influential figures in the cryptocurrency realm, utilizing social media platforms like X (formerly Twitter) and LinkedIn to promote the fake game. They employed generative AI and graphic designers to craft high-quality promotional material for DeTankZone and sent tailored emails masquerading as blockchain firms or game developers to potential targets.
The DeTankZone website was found to be constructed using stolen source code from a legitimate blockchain game called DeFiTankLand (DFTL), which suffered a security breach in March 2024 resulting in the theft of $20,000 worth of cryptocurrency. While the original developers suspected insider involvement, Kaspersky researchers suspect Lazarus Group’s hand in both the theft and the repurposing of the source code.
This incident underscores the evolving strategies employed by Lazarus Group and serves as a stark reminder to exercise caution when presented with unsolicited investment opportunities, especially those involving downloadable game clients or suspicious social media promotions. It is imperative to keep browser software updated with the latest security patches to minimize the risk of falling victim to zero-day exploits.